Internet Creations Security Expert Warns of Costly Effects of Ignoring Cyber Threats

One Wrong Click May Give Cyber Thieves Direct Access to Your Information
By Bari Faye Siegel
Failing to take action to secure your company’s IT infrastructure can be an expensive mistake. The estimated financial burden of global cybercrime is as much as $100 billion annually. In smaller operations, however, perhaps even more costly is the price of losing a customer’s trust when their information is compromised.
With major incidents of cybercrime still fresh in our memories (think Target, Sony, Home Depot), it’s easy to believe your company might be safe from online thieves. After all, why would hackers be wasting their time with you when there are so many bigger targets? Who knows, perhaps you’re right.
However, hackers aren’t your problem. Your real concern are the people sitting all around you; the fact is that most people turn a blind eye to the actual threats in plain sight.
“The problem isn’t hacking. User mistakes are our biggest problem,” Chris Ferraro, chief IT architect at Internet Creations, told the audience at a recent Salesforce New Jersey User Group presentation (Securing Your Salesforce Org: The Human Factor) held at IC’s headquarters in Hamilton. “Your users are presented with potential security threats all the time. Their actions are certainly not intentional, but a wrong click can wreak havoc on your system.”
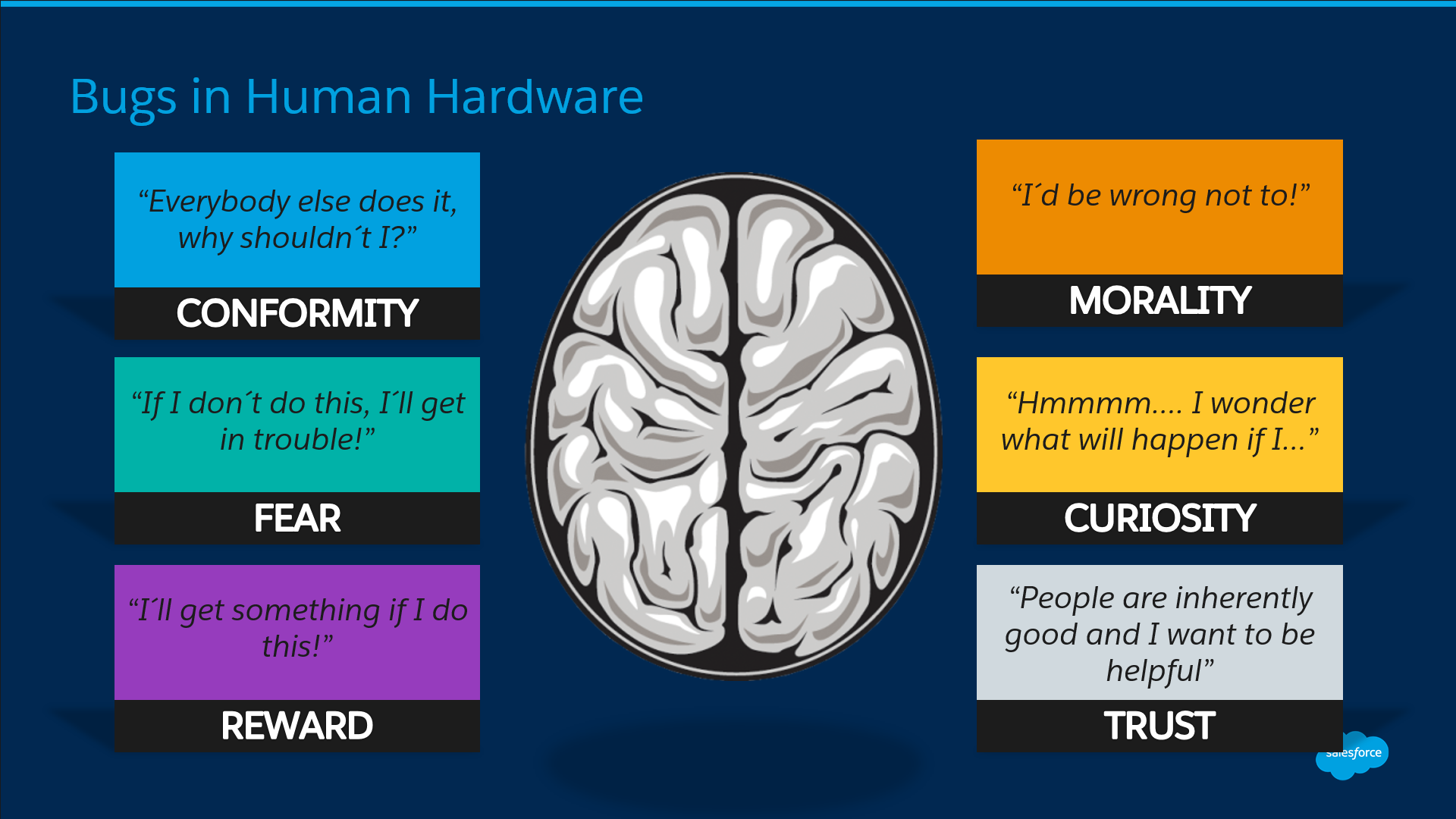
Ferraro explained that fear, curiosity and trust play a big role in a user’s decision to open an email or follow a link that leads into a dark unsecured hole. All the software in the world won’t help you if a colleague is duped into opening the proverbial door to cybercrime. And, once that door is open, cybercriminals sneak in and have access to all your information.
Ferraro shared the results of an experiment he and the IT team at Internet Creations conducted a few weeks prior to the User Group event. A bogus email was purposely sent out to the IC staff to see if they would take the bait. A very small percentage of IC team members clicked on the test email proving, perhaps, that even the most well-informed users can be tricked by smart, scheming criminals. The test also proved that Rich Tepper, IC’s manager of IT Services, and his team have done a solid job warning the staff to think before they click but that constant reminders are critical to protecting the system.
Even extremely well-designed, secure networks have weak links. Ignoring `The Human Factor’ can be a huge mistake. New malware and phishing concepts are created every day. The common response to questions about phishing or malware is `I would never fall for it.’ But even the smartest people do — every single day.
If members of your team received suspicious emails, would they be able to act quickly enough to hit `delete’ rather than `open?’
Find out how safe your organization’s IT system really is right now. Contact IT Services @ Internet Creations to learn more about how we can perform a FREE email security test and risk assessment for your company.
Knowledge is Power
To understand how to best advise users to take the proper precautions, it’s important to know the many potential entry points cyber criminals may use to infiltrate even the most guarded IT infrastructure.
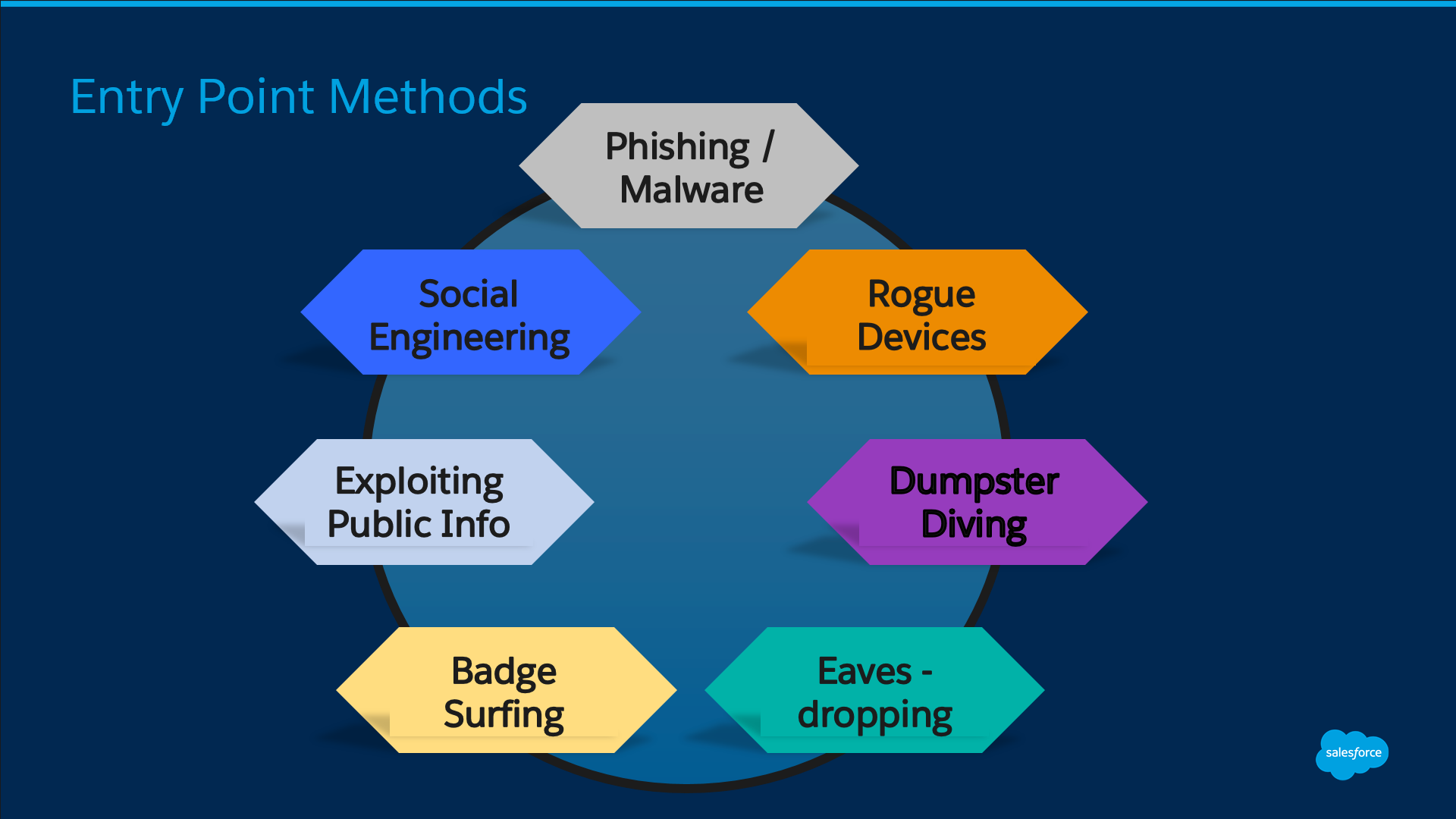
- But the email looked so real: Criminals are great at what they do, until they get caught. Therefore, it’s important to know that a fake email designed to convince a user to give away their password is going to look very real. Phishing and malware schemes are rampant these days. Of course, obvious typos, poor grammar and any request for money should be red flags to all users. Delete!
Real life example: IRS scams are rampant and they are coming at people fast and furiously through emails and phone calls. Many people have ended up on the wrong side of these cyberattacks, carefully designed to coincide with tax season. Read more.
- Bugs in the Human Hardware: Social engineering is actually a complex con game in which thieves attempt to obtain information (usually by phone) that would give them access to your online world. Don’t talk to strangers!
Real life example: If someone from Microsoft called to request remote access to your computer to fix a bug, what would you do? It can happen. Read more.
- The devil you don’t really know: Cybercriminals know users are leery and that’s why it’s easy to obtain public information and exploit it. It’s not uncommon for an email to appear to be coming from someone you know and would not ignore. For example, most people wouldn’t hesitate to respond to a legitimate-looking email from their boss or their bank.
Real life example: At Internet Creations, CFO Jade Brophy recently received an email from her CEO Chad Meyer asking her to wire money to a new international vendor. Brophy was suspicious and rightly so. Since Meyer was coincidentally out of town at the time Brophy received the bogus email, she reached out to him to confirm it wasn’t a legitimate request.
- Low Tech, High Returns: Believe it or not, dumpster diving and eavesdropping are two popular methods cybercriminals use to get access to your information. Always shred sensitive documents and don’t share your personal identification information with anyone.
Real Life Tip: There is absolutely no reason anyone needs to know your password – this includes your IT admin, Ferraro advised. “If access to your account is needed for a real reason, the IT department can reset access. They won’t need to know your personal password.”
As humans, we are naturally trusting. Cybercriminals prey on the human experience. “Often, a company’s technology is strong and secure. But people can be easily exploited. People, unfortunately, are often the weakest link,” Ferraro said.
Fight Back with Education: 3 Ways to Tighten Up Your IT Security
Through a series of exercises designed to raise awareness of difficult-to-spot phishing and other cyberattacks, many User Group attendees came face-to-face with reality. Most said their organizations had been continually educating team members about password security and cyber scam mindfulness. Still, far too many admitted they’ve encountered security breaches due to user error.

Get smart with passwords: In addition to keeping passwords private, many operations experience failures in the “don’t ask, don’t tell” world of cybersecurity. Therefore, take your password rules up a notch.
- Insist that your team use a two-factor authentication process that forces the system to double check the user. For example, a two-factor process could include a password (something the user knows) and a phone verification (which requires something the user is in possession of). Someone trying to gain entry under false pretenses might have the person’s password, but without their phone, in this example, authentication would fail.
- Activate password complexity and rotation rules: insist on a mix of letters and numbers, make sure passwords are at least eight characters in length and encourage forced password resets regularly (every 90 days is recommended.)
- Use LastPass or another strong password manager
Continued education is required to keep these cyber threats front and center for every member of your company with access to the system. “You can repeat the same information over and over and some people may not listen,” Ferraro told the IT leaders. “Still, you have to keep telling them.”
It’s up to the company’s IT team to provide all users – and constantly remind them – to be secure. “Don’t assume someone knows even the basics about cybersecurity,” Ferraro warned. “People are not malicious; they may just not know better. Be safe rather than sorry and tell them. And, then, tell them again.”
Learn more about how you can protect your business by downloading our Cyber Security Ebook
- Welcome to Dreamforce: You Have Arrived - October 1, 2016
- Now That’s Something to Brag About… - September 21, 2016
- IT Pros, Business Gurus, etc.: How Salesforce Admins Bring Them All Together - July 20, 2016


